NERD TALK requires more espresso. And since it’s late, ahem early am and we are up wrestling technical fun time warps, I’ll save my eloquent thoughts for the mid morning first jumpstart shot of caffeine. Thank you Sidecar, Stumptown, Rose Park, and even in the pinch, Starbucks for the assists.
NERD TALK requires more espresso. And since it’s late, ahem early am and we are up wrestling technical fun time warps, I’ll save my eloquent thoughts for the mid morning first jumpstart shot of caffeine. Thank you Sidecar, Stumptown, Rose Park, and even in the pinch, Starbucks for the assists.
+ | shew |
UPDATE 15.48 | A Nice SRP Circumventing Trick | During a recent penetration test, my goal was to smuggle data around out of a hardened virtual application. This particular test, included a vApp designed to restrict everything not needed to display and edit a Word document. Between Group Policy Objects and Software Restriction Policies, there were practically no third-party applications available to manipulate, and most Windows internal programs were either removed or hijacked by a Digital Rights Management DLL.
I’ll explain the trick that allowed me to execute around a Windows Software Restriction Policy (SRP) which was implemented via Group Policy Object (GPO) and applied to computers in the Active Directory domain. This policy prevented execution of C:\WINDOWS\System32\cmd.exe.
I took advantage of the rundll32.exe command to launch cmd.exe for me. This can be used for any DLL, but I was limited to system DLLs remaining on the box, and so far was unable to upload in anything like Didier Steven’s cmd.dll (http://blog.didierstevens.com/2010/02/04/cmd-dll/).
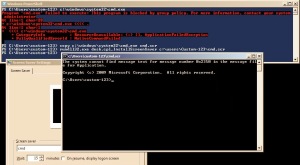
A screenshot below from a Server 2008 R2 box shows the technique. Basically, the rundll32.exe is allowed to run services and we can use it to call any library function from a DLL. Screensavers with the SCR file extension are still Portable Executable files, much like EXE. By making a copy of cmd.exe as cmd.scr, we can have rundll32.exe execute a shell for us. This technique is great for running most EXEs specifically denied via SRP:
copy c:\windows\system32\cmd.exe c:\temp\cmd.scr
rundll32.exe desk.cpl,InstallScreenSaver c:\temp\cmd.scr
Here, I demonstrate in PowerShell just because I like the readability of the error messages:
If you find this interesting or useful, then you’ll enjoy the entire SANS Security 660 Advanced Penetration Testing and Ethical Hacking course. https://www.sans.org/find-training/index/5886527/direct/#results